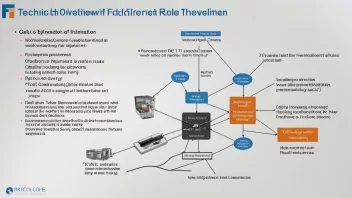
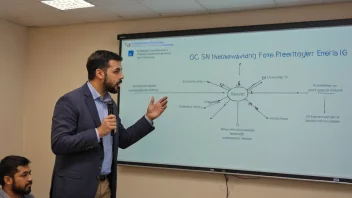
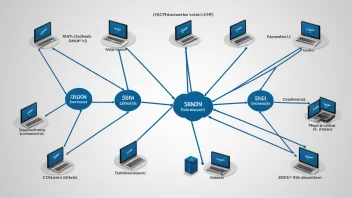
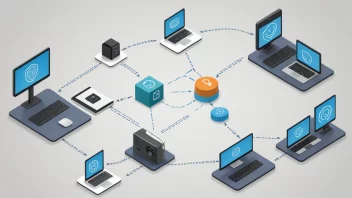
technology
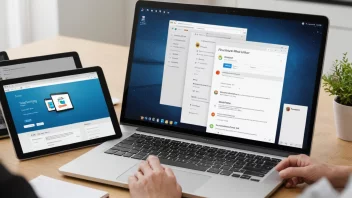
Technology encompasses a wide range of tools, techniques, and processes that are crucial in the modern world. From communication devices to complex algorithms, technology shapes how we interact, learn, and conduct business.
Artificial Intelligence Ethics
The Ethics of AI in Space Exploration: A Fictional Interview with Dr. Amelia Stark

Artificial Intelligence Ethics
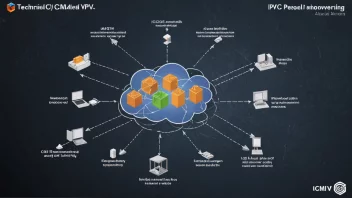
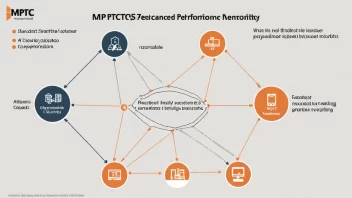
The Ethics of AI in Telecommunications: A Hypothetical Expert Interview

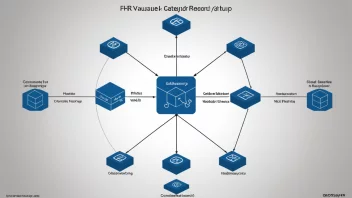
Software Development Practices
Best Practices for Writing Clean Code: Insights from a Fictional Expert