cybersecurity
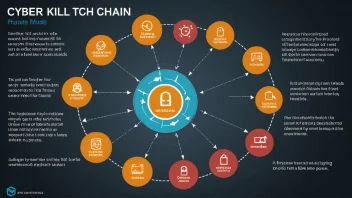
Cybersecurity is the practice of protecting computers, networks, and data from unauthorized access or criminal use. With the growth of the internet and reliance on digital technologies, cybersecurity has become critical for protecting sensitive information and maintaining privacy.
Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Applications in Blockchain, Data Integrity, and Password Storage

Software Development Practices
The Essential Role of Cryptographic Hashing Algorithms in Modern Technology