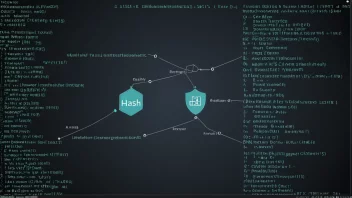
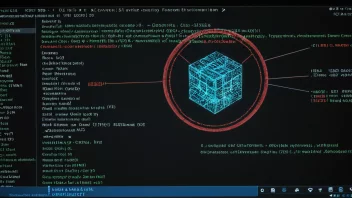
SHA-256
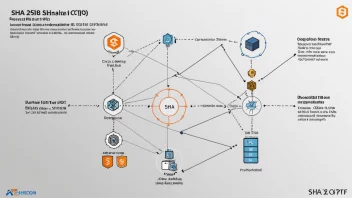
SHA-256 is a cryptographic hashing algorithm that produces a 256-bit hash value. It is widely employed in various security applications and protocols, including SSL, TLS, and blockchain systems for data integrity and authentication.
Artificial Intelligence Ethics
How to Implement Cryptographic Hashing Algorithms in Your Applications
Artificial Intelligence Ethics
Cryptographic Hashing Algorithms: A Comparative Analysis of SHA-256 and SHA-3
Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Key Concepts and Applications
Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Applications in Blockchain, Data Integrity, and Password Storage

Software Development Practices
The Essential Role of Cryptographic Hashing Algorithms in Modern Technology