Digital Signatures
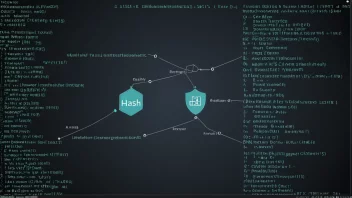
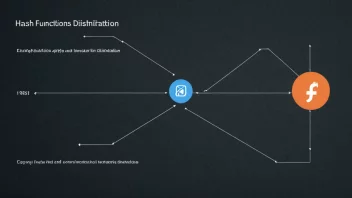
Digital signatures provide a way to confirm the authenticity and integrity of digital messages or documents. They utilize cryptographic techniques to ensure that a signature cannot be forged or altered, making them crucial in legal and financial transactions.