Cryptography
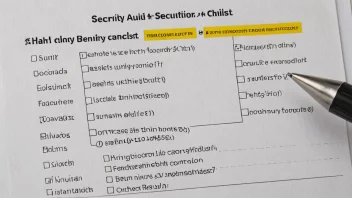
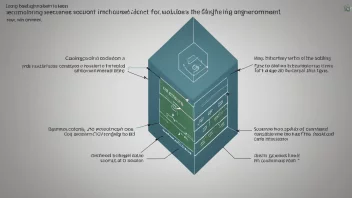
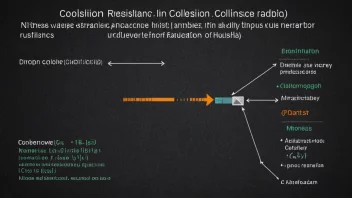
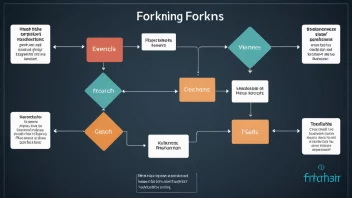
Cryptography is the practice of securing information by transforming it into a format that is unreadable to unauthorized users. It encompasses various methods and techniques, including encryption, hashing, and digital signatures, and is essential for secure communication in the digital age. Cryptography provides the foundation for securing sensitive data, powering technologies such as secure transactions, online privacy, and data integrity.