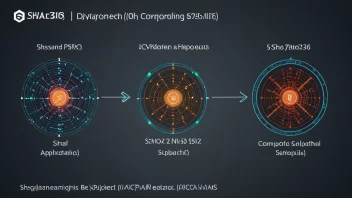
SHA-3
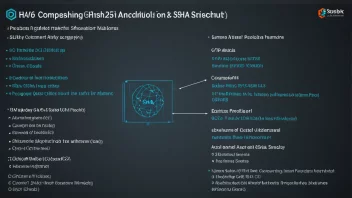
SHA-3 (Secure Hash Algorithm 3), based on the Keccak function, is the latest hashing algorithm standardized by NIST. It provides enhanced security and flexibility compared to its predecessors and is used in various applications that require strong cryptographic protections.
Artificial Intelligence Ethics
Cryptographic Hashing Algorithms: A Comparative Analysis of SHA-256 and SHA-3
Artificial Intelligence Ethics
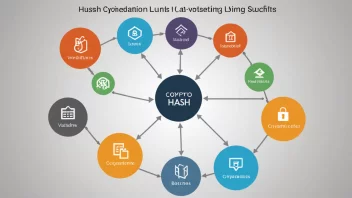
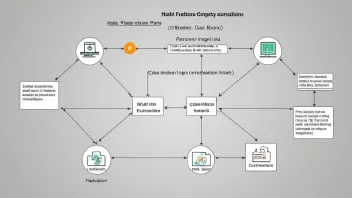
Understanding Cryptographic Hashing Algorithms: Applications in Blockchain, Data Integrity, and Password Storage