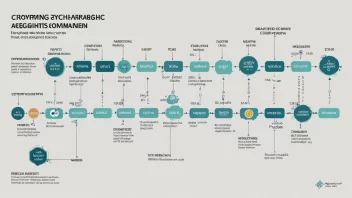
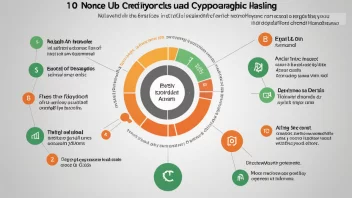
Cryptographic Hashing
Cryptographic hashing is a fundamental concept in cybersecurity and blockchain technology that ensures data integrity and secure data storage. By transforming input data into a fixed-length string of characters, hashing algorithms help authenticate information and validate transactions in digital ecosystems.
Artificial Intelligence Ethics
How to Implement Cryptographic Hashing Algorithms in Your Applications
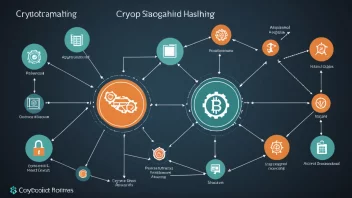
Artificial Intelligence Ethics
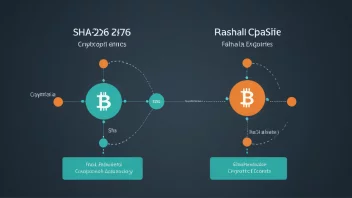
Cryptographic Hashing Algorithms: A Comparative Analysis of SHA-256 and SHA-3
Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Key Concepts and Applications
Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Applications in Blockchain, Data Integrity, and Password Storage

Software Development Practices
The Essential Role of Cryptographic Hashing Algorithms in Modern Technology