blockchain technology
Blockchain technology is a decentralized system that maintains a secure and tamper-proof record of transactions across multiple computers. This tag covers the fundamentals of blockchain, its various applications in sectors like finance, healthcare, and supply chain management, and the implications of this technology for transparency and security.
Artificial Intelligence Ethics
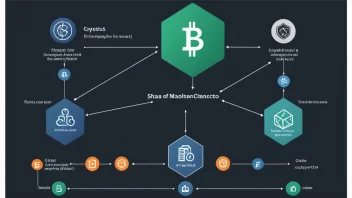
Understanding Cryptographic Hashing Algorithms: Applications and Implications

Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms in Blockchain Technology
Artificial Intelligence Ethics
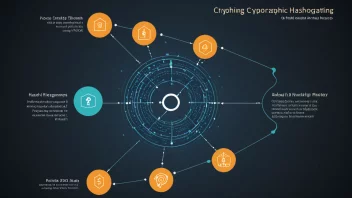
How to Implement Cryptographic Hashing Algorithms in Your Applications
Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Key Concepts and Applications
Artificial Intelligence Ethics
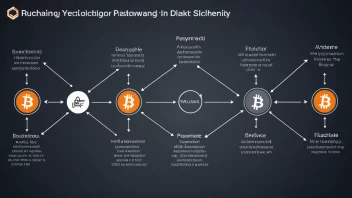
Understanding Cryptographic Hashing Algorithms: Applications in Blockchain, Data Integrity, and Password Storage

Software Development Practices
The Essential Role of Cryptographic Hashing Algorithms in Modern Technology