Cryptographic Algorithms
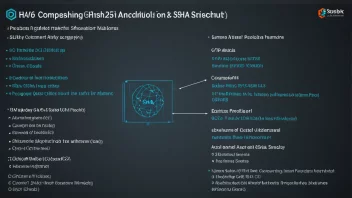
Cryptographic algorithms are crucial for securing information and ensuring privacy in digital communications. From hash functions to encryption methods, understanding these algorithms is key to designing robust security systems.