compliance
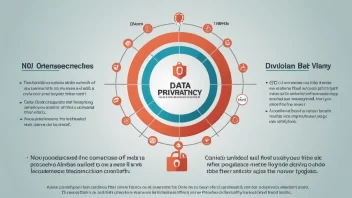
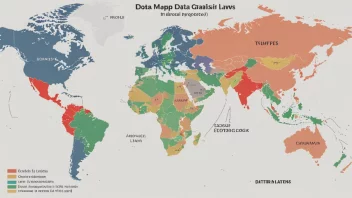
Compliance refers to the process of adhering to established guidelines or specifications, often set forth by governing bodies. This tag discusses various compliance aspects such as data protection, industry-specific regulations, and best practices that organizations can adopt to ensure they meet legal and ethical standards.