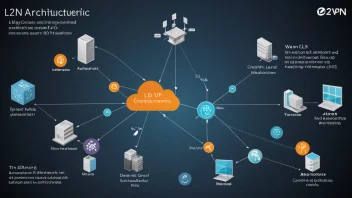
In today's increasingly interconnected world, the reliance on networked systems has grown significantly. This dependence makes organizations vulnerable to disruptions caused by natural disasters, cyberattacks, or other unforeseen events. Therefore, having a robust disaster recovery plan is essential for maintaining business continuity. Network protocols, which govern how data is transmitted and communicated over networks, play a pivotal role in ensuring that recovery processes are swift and effective. Understanding their importance can be the difference between a business's survival and its downfall in the wake of a disaster.
Understanding Network Protocols
Network protocols are sets of rules and standards that determine how network devices communicate with each other. They ensure data integrity, format, and transmission, allowing different systems and hardware to work together seamlessly. Common examples include Transmission Control Protocol/Internet Protocol (TCP/IP), Hypertext Transfer Protocol (HTTP), and File Transfer Protocol (FTP). Each of these protocols serves a distinct purpose and supports various applications, enabling the transmission of different types of data across local and wide-area networks.
The Role of Network Protocols in Disaster Recovery
Effective disaster recovery hinges on the ability to quickly and reliably restore IT systems and operations after a disruption. Network protocols facilitate this process by ensuring that data can be restored from backups, systems can be unified, and communication remains stable throughout the recovery. Without standardized protocols, recovery efforts can become chaotic, leading to delays that can harm an organization's long-term viability.
1. Data Synchronization and Backup
One of the primary functions of network protocols in disaster recovery is to facilitate data synchronization and backup. Using protocols such as the Network File System (NFS) or Secure Copy Protocol (SCP), organizations can ensure that their critical data is backed up in real-time or on scheduled intervals. This way, in the event of a disaster, the latest versions of files and databases can be restored quickly, reducing downtime and data loss.
2. Communication During a Crisis
During a disaster, internal and external communication is crucial. Network protocols such as VoIP (Voice over Internet Protocol) and Instant Messaging Protocols allow for seamless communication among team members and stakeholders. Additionally, these protocols facilitate important announcements and updates, ensuring that all parties are aligned and informed about the situation, which is essential for decision-making and coordinating recovery efforts.
3. Remote Access and Control
Network protocols enable secure remote access to systems, allowing IT professionals to manage and recover networked resources from offsite locations. Protocols like Virtual Private Network (VPN) and Secure Socket Layer (SSL) provide secure channels for remote administration. This means that even if the physical location is compromised, the IT team can still execute recovery plans and restore operations efficiently.
Case Studies of Network Protocols in Action
Case Study 1: Hurricane Disaster Recovery
In 2019, a financial services company faced a significant challenge when Hurricane Dorian threatened its regional headquarters. With a robust disaster recovery plan grounded in established network protocols, the organization had a clear action plan. They utilized VPN protocols to ensure that employees could work remotely and access essential files stored in the cloud. Additionally, backup data was synchronized using SCP, ensuring minimal data loss. The effective use of network protocols enabled the company to resume operations with only a few hours of downtime.
Case Study 2: Cyberattack Recovery
In another example, a healthcare provider was the target of a cyber attack that encrypted its systems, leading to a full operational halt. Fortunately, the organization had previously established a disaster recovery plan leveraging TCP/IP for data exchange among decentralized backups located offsite. Their backup systems had been regularly updated and were promptly restored thanks to the effective role of network protocols. The health organization was able to recover within 48 hours, upholding patient services and data privacy.
Best Practices for Implementing Network Protocols in Disaster Recovery
- Develop a Comprehensive Disaster Recovery Plan: Document protocols and procedures that incorporate the use of various network protocols for data recovery, communication, and remote access.
- Regularly Test Protocols: Conduct drills to assess the effectiveness of network protocols during simulated disasters. This helps identify bottlenecks and areas for improvement.
- Ensure Redundancy: Implement redundant systems and data backups across different geographical regions to enhance the overall resilience of the network.
- Stay Updated: Keep network protocols updated to incorporate the latest security features and ensure compatibility with new technologies.
- Train Staff: Provide ongoing training for employees on using network protocols effectively during a disaster recovery event to ensure swift execution of recovery plans.
Conclusion
The importance of network protocols in disaster recovery cannot be overstated. As organizations navigate the complexities of modern-day risks, the need for well-defined communication and data recovery steps becomes increasingly essential. By understanding and implementing effective network protocols, organizations can enhance their ability to respond to disasters, maintain business continuity, and safeguard critical information assets. The cases illustrated highlight that when network protocols are prioritized in disaster recovery planning, organizations are not only prepared to mitigate damage but are also positioned to recover quickly and effectively, ultimately ensuring their long-term sustainability in a precarious environment.