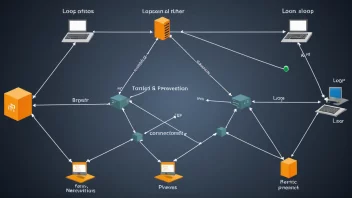
In the ever-evolving landscape of network security, the Extensible Authentication Protocol (EAP) plays a vital role in safeguarding access control across various networks. EAP is a flexible authentication framework that allows multiple authentication methods to be used, enabling secure connections and protecting sensitive data. This article delves into the frequently asked questions (FAQs) surrounding EAP and its implementation in network access control.
What is EAP?
EAP stands for Extensible Authentication Protocol, which is an authentication framework used in network protocols to facilitate secure communication between devices and servers. It is widely used in wireless networks, virtual private networks (VPNs), and point-to-point connections.
How does EAP work?
When a device attempts to connect to a network, EAP enables the exchange of authentication messages between the client and the authentication server. This process typically involves:
- The client requests access to the network.
- The server challenges the client to provide credentials.
- The client submits its credentials, which may include passwords, certificates, or biometric data.
- The server validates the credentials, and if successful, grants access.
What are the key types of EAP methods?
Several EAP methods are commonly used, each suited for different authentication scenarios:
- EAP-TLS: Utilizes Transport Layer Security for mutual authentication between the client and server, relying on X.509 certificates.
- EAP-PEAP: Stands for Protected EAP, a variation that creates a secure tunnel for password authentication, protecting credentials from exposure.
- EAP-TTLS: Similar to PEAP but allows for legacy authentication methods like PAP to be used inside the secure tunnel.
- EAP-FAST: Developed by Cisco, this method uses a Protected Access Credential (PAC) to create a secure tunnel for client authentication.
Why is EAP important for network access control?
The significance of EAP in network access control stems from its ability to provide:
- Flexibility: The varied authentication methods allow organizations to choose the most suitable method based on their security needs.
- Security: EAP methods like EAP-TLS implement strong encryption and secure authentication processes to protect sensitive data.
- Scalability: EAP can accommodate various network sizes and can easily integrate with existing infrastructure.
What challenges are associated with EAP?
While EAP offers several benefits, it also presents some challenges:
- Complexity: Implementing EAP can involve complex configuration, especially when dealing with multiple EAP methods.
- Certificate Management: In EAP-TLS and similar methods, managing certificates can be a logistical challenge for organizations.
- Compatibility: Not all devices support all EAP methods, which can lead to compatibility issues across different hardware and software.
How does EAP integrate with other security protocols?
EAP is often employed alongside other security protocols to enhance network access control. For example:
- RADIUS: EAP is frequently used with RADIUS (Remote Authentication Dial-In User Service) servers for centralized authentication management.
- IEEE 802.1X: This standard outlines the port-based network access control mechanism, where EAP functions as the method for authenticating users or devices trying to gain access to the LAN.
What are some real-world applications of EAP?
Businesses and institutions use EAP across various scenarios, including:
- Enterprise Wi-Fi networks: Companies implement EAP methods to secure access to internal wireless networks.
- Educational campuses: Universities utilize EAP to manage and protect the access of thousands of devices connecting to their networks.
- Healthcare: Hospitals leverage EAP for secure mobile device management and patient data protection.
In conclusion, the Extensible Authentication Protocol (EAP) is critical for network access control, providing a flexible and secure framework for authenticating users and devices. As the need for robust security measures continues to grow in our interconnected world, understanding and implementing EAP will be essential for organizations aiming to safeguard their network environments effectively.