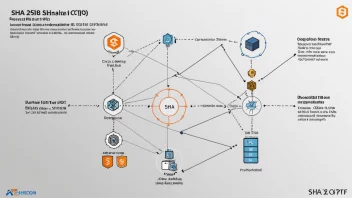
In today’s digital landscape, the need for security, integrity, and trustworthiness in data storage and transmission has never been more critical. Cryptographic hashing algorithms play a pivotal role in ensuring that data remains unaltered and secure from unauthorized access. These algorithms convert input data into a fixed-size string of characters, which appears random. The significance of cryptographic hashing transcends mere data protection; it underpins vital technologies like blockchain, enhances data integrity, and secures password storage. This article delves into the mechanics of cryptographic hashing algorithms, their applications, and their relevance in contemporary technological solutions.
Understanding Cryptographic Hashing Algorithms
At their core, cryptographic hashing algorithms are designed to take an input (or 'message') and produce a fixed-size string of bytes. The output, known as the hash value or hash code, is unique to each unique input. Minor changes to the input lead to significant changes in the hash, making it nearly impossible to derive the original input from the hash alone. Some of the most widely used hashing algorithms include SHA-256, SHA-3, and MD5, although the latter is often criticized for its vulnerabilities.
Key Properties of Cryptographic Hash Functions
Cryptographic hash functions are characterized by several critical properties:
- Deterministic: The same input will always produce the same hash output.
- Pre-image Resistance: It should be computationally infeasible to reverse the hash to retrieve the original input.
- Collision Resistance: It should be hard to find two different inputs that produce the same hash output.
- Small Changes Result in Large Differences: A minor alteration in the input should yield a drastically different hash.
Applications in Blockchain Technology
Blockchain technology relies heavily on cryptographic hashing algorithms to maintain security and integrity across decentralized networks. Each block in a blockchain contains a hash of the previous block, thereby linking them together in a secure chain. This mechanism ensures that if any block is altered, its hash changes, causing a ripple effect that invalidates all subsequent blocks. As a result, malicious actors cannot modify any data without being detected.
Case Study: Bitcoin
Bitcoin, the pioneering cryptocurrency, utilizes the SHA-256 hashing algorithm to secure transactions and generate new blocks. When miners validate a block of transactions, they must solve a complex mathematical puzzle that involves finding a hash that meets specific criteria. This process is known as Proof of Work and requires significant computational resources, which further enhances the security of the network.
Ensuring Data Integrity
Beyond blockchain, cryptographic hashing is integral in various data integrity applications. In software distribution, for instance, developers often provide hash values for downloads. Users can compute the hash of their downloaded files and compare it with the provided hash. If they match, it assures users that the file has not been tampered with during transmission.
Case Study: Software Updates
Consider a software company that releases a new update. To ensure users that the update is legitimate and has not been altered, they publish an SHA-256 hash of the update file. Users can verify the integrity of the update by calculating the hash of their downloaded file. If the hashes match, users can confidently install the update.
Password Storage and Security
Another critical application of cryptographic hashing algorithms is in the secure storage of passwords. Storing passwords in plain text is a significant security risk; if a database is compromised, all user credentials are exposed. Instead, organizations use hashing algorithms to store only the hash of passwords. When a user logs in, the system hashes the input password and compares it with the stored hash. If they match, access is granted.
Best Practices for Password Hashing
While hashing provides a layer of security, it is essential to employ best practices:
- Use Strong Hashing Algorithms: Prefer algorithms like bcrypt or Argon2, which are designed for password hashing and include features like salting.
- Salting: Adding a unique random string (salt) to each password before hashing ensures that even identical passwords produce different hashes.
- Iterative Hashing: Implementing a process that applies the hashing function multiple times significantly increases the time required to crack passwords.
Challenges and Future Directions
Despite their effectiveness, cryptographic hashing algorithms are not without challenges. The increasing computational power of modern hardware can lead to potential vulnerabilities, especially for older algorithms like MD5 and SHA-1. As a result, there is a constant need for research and development of more secure hashing algorithms. Emerging technologies like quantum computing pose further challenges, as they could potentially break current cryptographic standards.
Looking Ahead
The future of cryptographic hashing lies in developing algorithms that can withstand the potential threats posed by quantum computing. Researchers are actively working on quantum-resistant hashing algorithms that will secure data against the capabilities of quantum machines.
Conclusion
Cryptographic hashing algorithms are foundational to securing our digital world. From blockchain technology to data integrity checks and password storage, their applications are vast and essential. As technology evolves, so too must our approaches to hashing, ensuring that we remain one step ahead of emerging threats. Understanding these algorithms not only enhances our security measures but also empowers us to navigate the complexities of the digital age with confidence.