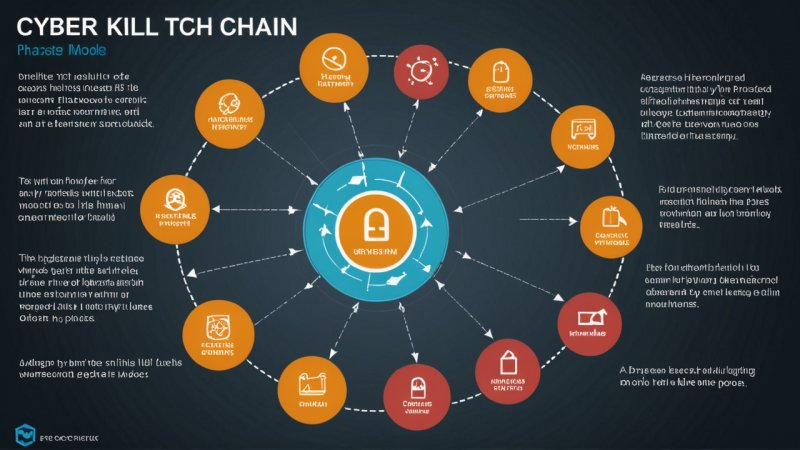
The Cyber Kill Chain is a model developed by Lockheed Martin that outlines the stages of a cyber attack. It provides a clear framework for understanding how attacks are planned, executed, and ultimately thwarted. As cyber threats become increasingly sophisticated, it's crucial for organizations to comprehend this model to enhance their defensive strategies.
The model is divided into seven distinct phases: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command & Control, and Actions on Objectives. Each phase represents a step an attacker must take to successfully compromise a target.
The first phase, Reconnaissance, involves gathering information about the target. Attackers utilize various techniques to identify potential vulnerabilities, such as social engineering, scanning open ports, and researching publicly available data. The goal is to understand how to craft an attack that will have the highest likelihood of success.
Next is the Weaponization phase, where attackers create a payload, which could be a malicious software or phishing email, tailored to exploit the vulnerabilities identified during the reconnaissance phase. This careful preparation increases the chance of the attack’s success.
The third phase, Delivery, is the actual transmission of the weaponized payload to the target. This could take the form of an attachment in an email, a link in a message, or a direct intrusion into the network. Successful delivery is critical because if an organization has strong defenses, the attack may never reach its target.
When the payload arrives, the Exploitation phase occurs. This is where the attacker takes advantage of the vulnerability to execute the code or deploy malware. A successful exploitation often requires some form of user interaction or system configuration that allows malicious code to run.
Following exploitation, the Installation phase takes place. Here, the malware is installed on the target system, providing the attacker with a foothold within the network. This phase is pivotal because it eliminates the need for repeat exploitation attempts, allowing attackers to maintain access over time.
Once installed, attackers initiate Command & Control (C2), which allows them to communicate with the infected system and issue commands remotely. This step is critical for maneuvering within the compromised environment, enabling the attacker to move laterally across networks and escalate their permissions.
Finally, the Actions on Objectives phase is where the attacker achieves their ultimate goal, whether it’s exfiltrating data, disrupting services, or damaging reputations. Understanding this phase helps organizations recognize the importance of monitoring their systems for unusual activities that could signify an ongoing attack.
Implementing the Cyber Kill Chain model in a cybersecurity strategy can significantly enhance an organization's defenses. By recognizing each phase, security teams can develop proactive measures to disrupt attacks early in the process. For instance, increasing vigilance during the reconnaissance phase can help detect suspicious activities and reduce the likelihood of successful weaponization and delivery.
In conclusion, the Cyber Kill Chain provides a structured methodology to understand cyber attacks. By analyzing each stage, organizations can better prepare for potential threats. Awareness of this model not only helps in preventing attacks but also aids in responding more effectively when breaches do occur. Mastering the understanding of the Cyber Kill Chain model is critical for any organization looking to bolster its cybersecurity posture.