As emerging technologies continue to reshape the landscape of our daily lives, their integration into various sectors presents a host of opportunities and challenges. The rapid development of artificial intelligence, the Internet of Things (IoT), blockchain, and 5G technology offers the potential for increased efficiency, connectivity, and innovation. However, these technologies also introduce new vulnerabilities and risks, making cybersecurity a paramount concern. This article delves into the critical importance of cybersecurity in emerging technologies, exploring various aspects such as the nature of threats, the evolving landscape of security measures, and case studies that highlight real-world implications.
Understanding Emerging Technologies
Emerging technologies can be defined as those that are currently developing or will be developed over the next few years and have the potential to alter the technology landscape significantly. Some key players among these technologies include:
- Artificial Intelligence (AI): AI applications range from machine learning algorithms to natural language processing and robotics, bringing both transformative advantages and unique security challenges.
- Internet of Things (IoT): The interconnectivity of devices in IoT environments creates complexity that can introduce vulnerabilities if not secured properly.
- Blockchain: Known primarily for its application in cryptocurrencies, blockchain supports secure and transparent transactions but can also be targeted by cyber threats.
- 5G Technology: The transition to 5G networks improves speed and connectivity but raises concerns about the security of data transmission and device interactions.
The Cybersecurity Threat Landscape
With the growth of emerging technologies, the types of cyber threats have evolved significantly. Here are some of the most pressing concerns:
1. Increased Attack Surfaces
As more devices become interconnected, the potential points of exploitation for cybercriminals expand. Each IoT device can serve as an entry point for an attacker. Poorly secured devices can be turned into botnets, as seen in incidents like the Mirai botnet attack.
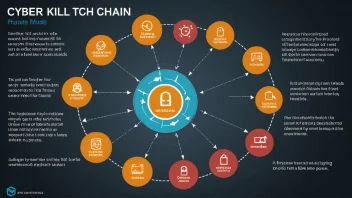
2. Advanced Persistent Threats (APTs)
APTs are prolonged and targeted cyberattacks in which intruders gain access to a network and remain undetected for long periods. This is particularly relevant in AI systems, where algorithms can be manipulated to produce harmful outcomes.
3. Ransomware Attacks
Ransomware continues to be a significant threat, with attackers increasingly targeting essential services and data within organizations reliant on emerging technologies. With the critical data stored on cloud services and IoT devices, the consequences of such attacks can be disastrous.
4. Supply Chain Vulnerabilities
As organizations increasingly rely on third-party vendors to develop and deploy technology solutions, vulnerabilities within the supply chain can further compromise the security of their overall systems. Examination of security protocols at all levels is necessary.
Implementing Cybersecurity Measures in Emerging Technologies
The integration of robust cybersecurity measures is essential to safeguard data and systems. Here are several strategies organizations can employ:
1. Risk Assessment
Organizations must conduct thorough risk assessments to identify potential vulnerabilities within their existing technology framework. This involves evaluating hardware, software, and human factors to anticipate potential threats.
2. Implementation of Security Protocols
Establishing stringent security protocols for data encryption, authentication, and access control is vital across all technology platforms. For example:
- AI: Implement adversarial training techniques to make models robust against malicious input.
- IoT: Enforce strong authentication procedures, such as multi-factor authentication, on all connected devices.
- Blockchain: Ensure that smart contracts are coded correctly to prevent exploitation.
- 5G: Utilize end-to-end encryption to secure data during transmission.
3. Employee Training and Awareness
Employees are often the first line of defense against cyber threats. Regular training sessions on cybersecurity best practices can help foster a culture of security-awareness within organizations.
4. Incident Response Plans
Organizations should develop and regularly update their incident response plans to ensure rapid, efficient reactions to cybersecurity incidents. This includes defining roles and responsibilities and conducting regular drills.
Case Studies: Real-World Applications of Cybersecurity in Emerging Technologies
Several organizations have taken significant steps to secure their systems in light of emerging technological threats:
1. Target: Ransomware and Operational Resilience
In 2020, Target faced a ransomware attack that threatened to halt its operations. By leveraging machine learning algorithms and robust recovery practices, they were able to mitigate the risks and reinforce their cybersecurity posture.
2. The SolarWinds Cyberattack
The SolarWinds incident exposed vulnerabilities in software supply-chain security. It highlighted the need for multi-layered security approaches and the importance of scrutinizing third-party vendors to enhance cybersecurity across entire industries.
3. The Mirai Botnet Attack
This event, which exploited unsecured IoT devices, serves as a stark reminder of the vulnerabilities inherent in connected systems. Its aftermath has led to enhanced discussions around developing security standards for IoT devices.
The Future of Cybersecurity in Emerging Technologies
Looking ahead, the landscape of cybersecurity will have to adapt continuously as technologies evolve. The advent of quantum computing, for example, may render traditional encryption techniques obsolete, necessitating new cryptographic approaches. Artificial intelligence will play an increasing role in both perpetrating and preventing cyberattacks, creating a cat-and-mouse game between adversaries and defenders.
Moreover, as regulations like the General Data Protection Regulation (GDPR) become more prevalent, organizations will need to prioritize compliance, making cybersecurity not just a technical challenge, but a legal obligation.
Conclusion
In conclusion, the importance of cybersecurity in the realm of emerging technologies cannot be overstated. As advancements in technology propel society forward, they simultaneously introduce significant risks that can jeopardize data integrity, privacy, and trust. By adopting comprehensive cybersecurity measures, organizations can protect their systems and stakeholders against evolving threats. The path forward involves a collaborative effort across sectors, emphasizing the need for robust security protocols, continuous training, and an adaptive response to potential threats. Recognizing the dual-edged nature of emerging technologies is crucial for ensuring their benefits can be fully realized without compromising safety and security.