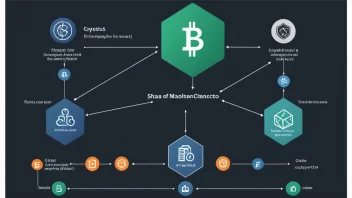
Cryptographic hashing algorithms play a crucial role in securing digital information, ensuring data integrity, and protecting sensitive information such as passwords. These algorithms take input data and produce a fixed-size string of characters, which is typically a hexadecimal number, uniquely representing the input. Given the increasing importance of cybersecurity in today's digital landscape, understanding how these algorithms work and their applications is imperative for anyone involved in technology, data protection, or security. Here are several key points that outline the significance of cryptographic hashing algorithms.
1. What is a Cryptographic Hashing Algorithm?
A cryptographic hashing algorithm is a mathematical function that transforms input data of any size into a fixed-size output. This output, known as a hash, is unique to each unique input. The primary characteristics of a secure hashing algorithm include:
- Deterministic: The same input will always produce the same output.
- Pre-image resistance: It should be infeasible to reverse-engineer the original input from its hash.
- Collision resistance: It should be unlikely for two different inputs to produce the same hash.
- Fast computation: Hashing should be computationally efficient.
- Small changes in input produce significant changes in output: Even minor alterations in input data should result in a completely different hash.
2. Applications in Blockchain Technology
Cryptographic hashing algorithms are foundational to blockchain technology. They ensure the integrity and security of blockchain transactions. Key applications include:
- Transaction Integrity: Each transaction on a blockchain is hashed, creating a unique identifier that helps prevent tampering.
- Block Hashing: A block in a blockchain contains the hash of the previous block, linking them securely and ensuring that altering one block necessitates changes to all subsequent blocks.
- Proof of Work: Many cryptocurrencies use hashing algorithms as part of their consensus mechanisms, where miners must solve complex hashing puzzles to validate transactions and create new blocks.
- Digital Signatures: Hashing algorithms are used in conjunction with public-key cryptography to create digital signatures, ensuring that transactions are genuine and authorized by the sender.
3. Ensuring Data Integrity
Data integrity is vital for maintaining the accuracy and consistency of information over its lifecycle. Cryptographic hashing algorithms contribute to this integrity in several ways:
- File Verification: Hashes can be used to verify that files remain unchanged. For example, software downloads often include checksums, allowing users to confirm that their downloaded file matches the expected hash.
- Data Deduplication: In data storage, hashing can help identify duplicate files, ensuring efficient use of resources.
- Version Control: In systems like Git, hashing helps track changes to files over time, allowing for robust version control and collaboration.
4. Password Storage
Storing passwords securely is a critical aspect of information security. Cryptographic hashing algorithms are often employed in this context:
- One-way Hashing: Passwords are hashed before storage, meaning that even if the database is compromised, the actual passwords are not exposed.
- Salting: Adding random data (salt) to passwords before hashing helps protect against rainbow table attacks, making it significantly harder for attackers to recover original passwords.
- Key Stretching: Techniques like PBKDF2, bcrypt, and scrypt use hashing algorithms to slow down the hashing process, making brute-force attacks more difficult.
5. Case Studies and Real-World Implementations
Numerous organizations leverage cryptographic hashing algorithms to enhance their security posture:
- Bitcoin: The SHA-256 hashing algorithm is integral to the Bitcoin blockchain, ensuring transaction security and integrity.
- Git: By using SHA-1 hashes, Git allows developers to efficiently manage changes and collaborate on projects.
- Secure Password Storage: Organizations like Dropbox and Twitter use bcrypt for hashing passwords, providing robust security against potential breaches.
In conclusion, cryptographic hashing algorithms are essential tools in the digital world, providing security, integrity, and efficiency across various applications. From ensuring the integrity of blockchain technology to protecting sensitive information like passwords, understanding these algorithms is crucial for anyone involved in digital security. As cybersecurity threats continue to evolve, the importance of robust hashing techniques will only increase, making it vital to stay informed and implement best practices.