In an increasingly digital world, the security of data has become a paramount concern. When it comes to safeguarding information, two prominent techniques often come into play: hashing and encryption. While these terms are frequently used interchangeably in casual dialogue, they represent fundamentally different concepts in the realm of cybersecurity. Understanding the distinction between hashing and encryption is essential for professionals and enthusiasts alike, as it impacts how we design secure systems and protect sensitive information. This article delves into the critical differences, applications, and implications of both methods, providing a comprehensive overview that sheds light on these crucial aspects of cryptographic security.
Defining Hashing
Hashing is the process of transforming input data into a fixed-size string of characters, which is typically a hexadecimal or binary representation. This transformation is achieved through a mathematical function known as a hash function. Hash functions take an input (or 'message') and produce a hash value, which serves as a unique identifier for that input. One of the key characteristics of a hash function is that it is a one-way process: it’s computationally infeasible to reverse-engineer the original input from its hash value.
Characteristics of Hash Functions
- Deterministic: The same input will always produce the same hash output.
- Fixed Size: Regardless of the input size, the hash output will always be of the same length. For example, SHA-256 generates a 256-bit hash.
- Fast Computation: Hash functions are designed to compute a hash value quickly.
- Collision Resistance: It is extremely unlikely for two different inputs to produce the same hash output.
Defining Encryption
Encryption, on the other hand, is a process that transforms data into a format that cannot be read by unauthorized users. This is accomplished by using an encryption algorithm and a key. The encrypted data, known as ciphertext, can only be reverted to its original form, known as plaintext, through decryption, which requires the appropriate key. Unlike hashing, encryption is a reversible process, meaning one can obtain the original data if one has the right key.
Characteristics of Encryption
- Reversible: Encrypted data can be decrypted back into its original form if the correct key is available.
- Variable Output Size: The size of the ciphertext can vary based on the algorithm and mode used.
- Key Dependence: Strong encryption relies on the security of the key, making key management critically important.
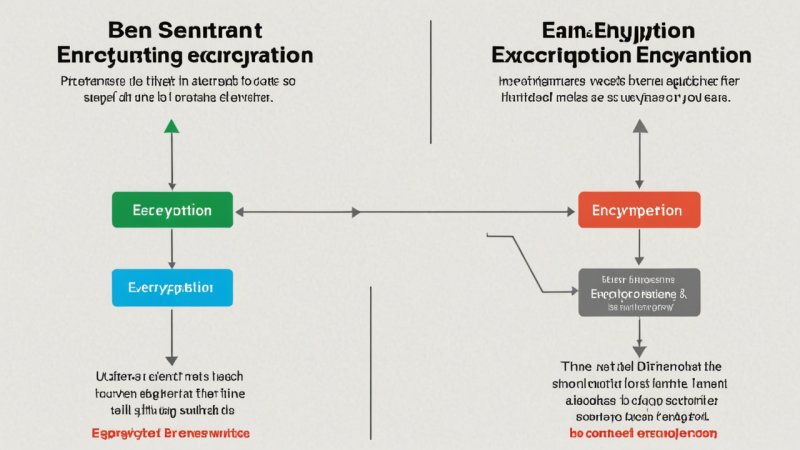
Key Differences Between Hashing and Encryption
While hashing and encryption are both integral to the field of cryptography, they differ in several fundamental ways:
- Purpose: Hashing is primarily used for data integrity verification, while encryption is used to protect the confidentiality of data.
- Reversibility: Hashing is a one-way function; encrypted data can be reversed back to its original form.
- Output Consistency: Hash outputs are always the same length, while encrypted outputs may vary in size.
- Use Cases: Hashing is commonly used in password storage, digital signatures, and data integrity checks; encryption is widely used for secure communication, file protection, and secure transactions.
Applications in Real-World Scenarios
Both hashing and encryption have significant applications across various sectors, with distinct use cases that underscore their respective functionalities.
Hashing Use Cases
- Password Storage: Websites commonly use hash functions to store passwords securely. Instead of saving the actual password, they store the hash, which protects against unauthorized access if the database is compromised.
- Data Integrity Checks: Hashing is also essential in verifying data integrity during transmission. For instance, file integrity can be confirmed by comparing hash values before and after transfer.
- Digital Signatures: Hash functions play a crucial role in generating digital signatures, where the hash of a document is encrypted to authenticate its integrity and authorship.
Encryption Use Cases
- Secure Communications: Protocols like HTTPS use encryption to secure data transmitted between a web server and a browser, ensuring that sensitive data like credit card information remains confidential.
- Data Protection: Organizations use encryption to protect sensitive files on devices and servers, safeguarding against unauthorized access in case of theft or hacking.
- Email Security: Encryption is often used in email communication to ensure only intended recipients can read the contents of messages, with methods such as PGP (Pretty Good Privacy) offering robust solutions.
The Importance of Key Management in Encryption
A crucial aspect of encryption is key management. The security of encrypted data heavily depends on the strength and confidentiality of the encryption keys. If an attacker gains access to the key, they can easily decrypt the data.
Principles of Effective Key Management
- Key Generation: Ensure that keys are generated using a strong, random process.
- Key Storage: Use secure methods for storing keys, such as hardware security modules (HSMs) or key management systems.
- Regular Rotation: Periodically rotate encryption keys to enhance security.
- Access Control: Limit access to keys to only those individuals who absolutely need it.
Conclusion
In summary, while both hashing and encryption serve essential roles in data security, they are fundamentally different in purpose and function. Hashing provides a way to ensure data integrity and is a one-way function that doesn’t allow recovery of original data, making it suitable for password storage and integrity checks. In contrast, encryption safeguards the privacy of information by allowing secure communication and reversibility, relying heavily on effective key management. Understanding these connotations is vital for anyone involved in data security, enabling better protection of sensitive information and informed choices in the cybersecurity landscape.