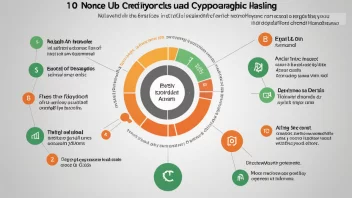
In the ever-evolving landscape of cybersecurity, the analysis of network traffic has emerged as a vital component in protecting data integrity and identifying potential breaches. One critical technology utilized in this process is cryptographic hashing, which plays a significant role in ensuring the authenticity and verification of data transmitted across networks. Hashing algorithms convert data into fixed-size hash values, enabling rapid data verification without exposing the original content. This article delves into the essential functions and advantages of hashing in network traffic analysis, shedding light on its importance in modern cybersecurity practices.
Data Integrity Verification
One major application of hashing in network traffic analysis is enhancing data integrity verification. When packets are transmitted over a network, they can be altered or tampered with during transit. By creating a hash of the original data before transmission, network administrators can compare the hash of the received data with the initially calculated hash. If the two hashes match, it confirms that the data arrived intact and unaltered, thus ensuring data integrity.
Efficient Anomaly Detection
Hashing also aids in facilitating efficient anomaly detection in network traffic. By using hashing algorithms, network monitoring tools can quickly compute and evaluate hashes for vast amounts of data. This not only expedites the process of determining whether packets are unusual but also helps in identifying patterns that might indicate malicious activities. Anomalies can include unexpected traffic spikes or unusual payload sizes, which can be flagged for further investigation.
Signature-Based Threat Detection
Hashing is a cornerstone for signature-based threat detection methods. In this context, well-known malware signatures are represented as hash values. Network traffic analysis tools can compare incoming files and data packets against a database of known malicious hashes, enabling rapid identification of threats. This approach is particularly effective in defending against previously documented threats that have clear signatures.
Streamlined Log Verification
Another significant benefit of using hashing in network traffic analysis is the streamlined verification of logs. Logs are essential for auditing and monitoring network activity, but their vast amounts can be cumbersome to analyze. Hashing each log entry allows network administrators to create hash trees, or Merkle trees, that summarize the integrity of entire log files. This technique ensures that any changes or deletions in logs can be easily detected by comparing the root hash, thus maintaining a forensic trail during security audits.
Secure Data Transmission
Lastly, hashing plays a vital role in secure data transmission protocols. When data is sent over potentially insecure channels, such as the internet, hashing can be used alongside encryption to protect sensitive information. By hashing the data before encryption, any alterations during transmission can be detected. Techniques like HMAC (Hash-based Message Authentication Code) combine hashing with a secret key, providing an additional layer of security for authenticating data during its exchange.
In conclusion, the role of cryptographic hashing in network traffic analysis cannot be overstated. It ensures data integrity verification, facilitates efficient anomaly detection, underpins signature-based threat detection, streamlines log verification, and enhances secure data transmission. As organizations continue to navigate the complexities of cybersecurity, understanding the nuances of cryptographic hashing will remain a crucial element in safeguarding digital assets and maintaining robust communication networks.