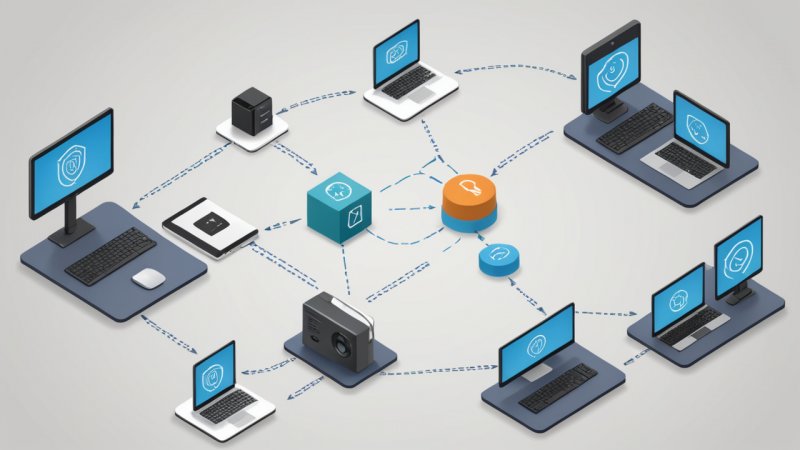
In the rapidly evolving landscape of the Internet of Things (IoT), security has become an ever-pressing concern. With numerous devices interconnected through the internet, the potential for vulnerabilities has dramatically increased. To shed light on this critical issue, we hypothetically interviewed Dr. Alice Harmon, a leading expert in cybersecurity and cryptographic algorithms. Dr. Harmon has over 15 years of experience in the field, focusing on the application of cryptography in securing IoT devices. This fictional interview aims to dive deep into the crucial role that hashing plays in ensuring the security and integrity of IoT systems.
Understanding Hashing in IoT
Interviewer: Dr. Harmon, can you explain what hashing is in the context of IoT devices?
Dr. Harmon: Absolutely! Hashing is a process that transforms any input data into a fixed-size string of characters, which is typically a sequence of numbers and letters. It serves various purposes, but in IoT, it is primarily used to ensure data integrity and secure communications. Given the resource constraints of IoT devices, efficient hashing algorithms like SHA-256 or BLAKE2 are favored due to their balance between security and performance.
The Importance of Data Integrity
Interviewer: Why is data integrity so vital in IoT applications?
Dr. Harmon: Data integrity is essential in IoT because these devices often collect and transmit sensitive information. An attack that manipulates data could lead to significant consequences, from incorrect weather readings affecting agriculture to tampered health-monitoring devices that can endanger lives. By utilizing hashing algorithms, devices can verify that their data has not been altered during transmission or storage. If the hash of the received data doesn't match the expected hash, the system knows that an error occurred or a malicious attack is at play.
Implementing Hashing Algorithms
Interviewer: Could you provide an overview of how to implement hashing in an IoT device?
Dr. Harmon: Certainly! Implementing hashing generally involves the following steps:
- Choose a Hashing Algorithm: Select an algorithm based on your needs—SHA-256 is widely used due to its robust security features, while BLAKE2 could be more suitable for low-latency operations.
- Input Data: Gather the data that needs to be hashed. This could be sensor readings, configuration files, or any data received from other devices.
- Compute the Hash: Use a cryptographic library in your device's programming language that supports the chosen algorithm to compute the hash.
- Store and Verify: Store the generated hash securely. When the same data needs to be validated, hash it again and compare it with the stored hash.
Real-World Applications and Case Studies
Interviewer: Can you share some real-world applications where hashing has enhanced IoT security?
Dr. Harmon: Certainly! One notable example is in smart home devices. For instance, a smart thermostat may use hashing to ensure that the data it receives from temperature sensors is genuine. If an attacker tries to spoof the data, the thermostat can detect the discrepancy by comparing hashes. Additionally, industrial IoT applications, such as in monitoring oil rigs, often use hashing to secure telemetry data transmitted to central systems, ensuring that operational data is unaltered and trustworthy.
Challenges and Future Directions
Interviewer: What challenges do you foresee in implementing hashing for IoT devices?
Dr. Harmon: One major challenge is the limited computational resources available on many IoT devices. While hashing algorithms like SHA-256 provide strong security, they also consume significant processing power, which can drain device batteries quickly. Moreover, the ever-evolving nature of cybersecurity threats means that hashing algorithms themselves must continue to evolve to stay one step ahead of attackers. As we look to the future, I predict the emergence of lightweight hashing techniques that maintain security without excessive resource usage.
Conclusion
The fictional insights shared by Dr. Alice Harmon emphasize the centrality of hashing in securing IoT devices. Through techniques that ensure data integrity and secure communications, hashing not only protects individual devices but also fortifies entire ecosystems against threats. As IoT continues to develop, the ongoing advancement in cryptographic algorithms, particularly in hashing, will be crucial. Understanding and implementing these techniques will be vital for stakeholders in the increasing interconnected world of IoT.