Introduction
Phishing attacks pose a significant threat in today's digital landscape, targeting individuals and organizations to steal sensitive information. One of the key techniques in combating phishing is the use of cryptographic hash functions. These algorithms not only enhance data integrity but also play a crucial role in securing communications and authentication processes. This article explores common questions regarding the role of hash functions in preventing phishing attacks.
What are hash functions?
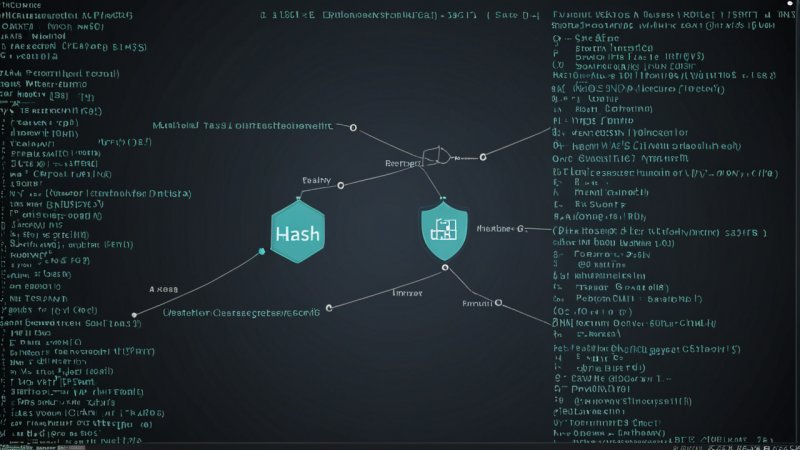
A hash function is a mathematical algorithm that transforms an input (or 'message') into a fixed-size string of bytes. The output, often called the hash value or hash code, is unique to each unique input. Hash functions are designed to be fast and efficient, making them ideal for a variety of applications, including data verification and security.
How do hash functions help prevent phishing attacks?
Hash functions help in several ways:
- Data Integrity: By generating a hash of the original data, any changes to that data can be easily detected. If the hash of the received data does not match the original, this indicates tampering.
- Secure Password Storage: Hash functions are used to hash passwords before storing them in databases. If a phishing attack compromises the database, attackers are left with hashed passwords, which are difficult to reverse-engineer.
- Digital Signatures: Hash functions are integral to creating digital signatures, which verify the authenticity of messages and documents, ensuring that they have not been altered by malicious actors.
What are some popular hash functions used in cybersecurity?
Several widely used hash functions include:
SHA-256: Part of the SHA-2 family, it produces a 256-bit hash and is commonly used in blockchain and data integrity verification.MD5: Although it has vulnerabilities, it was widely used for checksum verification before its weaknesses were exposed.Bcrypt: A password hashing function that incorporates a salt to protect against rainbow table attacks and allows for adaptive hashing.
What is the role of salting in hash functions?
Salting is the process of adding a random value (salt) to the input of a hash function before it is hashed. This ensures that even identical inputs will produce different hash values. Salting is particularly important in password storage as it mitigates the effectiveness of precomputed attacks (like rainbow tables) against hashed passwords.
Can hash functions be reversed or cracked?
Hash functions are designed to be one-way functions, meaning that they cannot be reversed. However, if the hash function is weak (like MD5) or if an attacker uses brute-force methods or precomputed hashes, they may be able to find a collision or guess the original input. This is why it's critical to use strong hash functions (e.g., SHA-256) and to implement salting and stretching techniques.
What are some real-world examples of hash functions preventing phishing?
Real-world applications of hash functions include:
- Blockchain Technology: Cryptocurrencies like Bitcoin use SHA-256 hashing to secure transactions and maintain integrity.
- Email Authentication: Protocols like SPF, DKIM, and DMARC utilize hash functions to verify the authenticity of emails and prevent phishing.
- Software Distribution: Hash functions are used to verify the integrity of downloaded software, ensuring that it has not been tampered with during transmission.
What should organizations do to protect against phishing attacks?
Organizations should consider the following measures:
- Implement strong password policies, using hashes and salts for storage.
- Use multi-factor authentication (MFA) to add an extra layer of security.
- Educate employees about phishing tactics and how to recognize suspicious communications.
- Regularly update and patch systems to protect against vulnerabilities.
Conclusion
Hash functions play a pivotal role in cybersecurity, particularly in preventing phishing attacks. By ensuring data integrity, securing password storage, and enabling digital signatures, they contribute significantly to overall security measures. Organizations must leverage these tools effectively, alongside other strategies, to create a robust defense against phishing threats.